In many organizations, cybersecurity discussions at the leadership level often sound reassuring. The Chief Information Security Officer (CISO) presents detailed reports highlighting compliance certifications, audit outcomes, and a strong portfolio of security tools. On paper, everything appears secure. Policies are documented, frameworks are followed, and investments have been made.
However, when a real ransomware attack begins spreading across systems, that confidence can quickly disappear. Teams may struggle to respond in a coordinated and decisive manner, and uncertainty replaces assurance. This exposes a clear gap between perceived readiness and actual operational capability.
The issue is not always a lack of technology. More often, it is a lack of operational confidence. Organizations invest heavily in infrastructure, but professionals managing these systems may still feel underprepared. The widening cybersecurity skills gap further limits how effectively teams can respond, even when advanced tools are in place.
To truly address this challenge, organizations must look beyond tools and compliance. They need to evaluate how security teams are trained, supported, and tested in real-world scenarios.

The Illusion of Compliance-Based Security
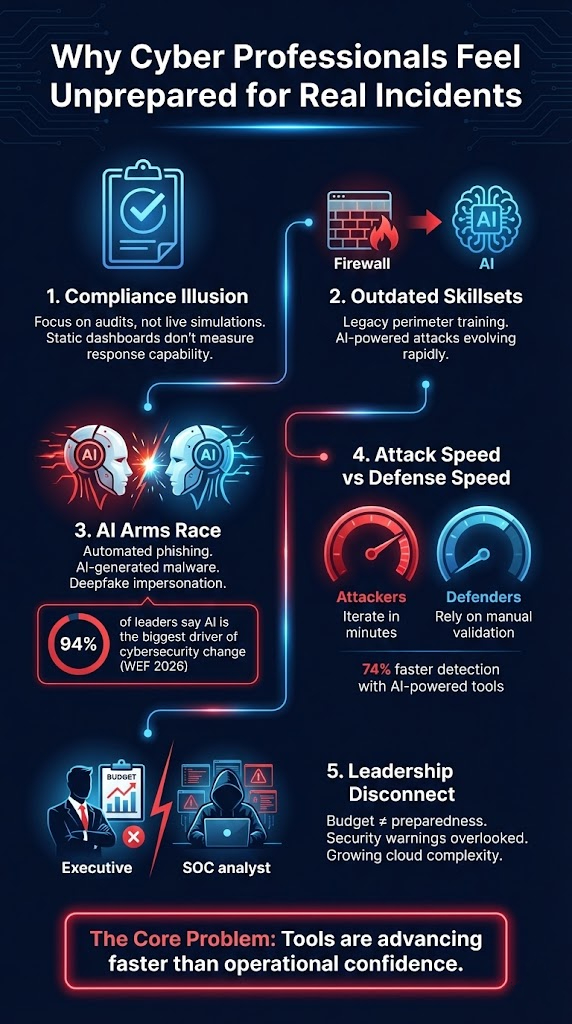
For years, many organizations have treated compliance as the main indicator of security. Certifications such as ISO or SOC2 are important for business credibility and regulatory requirements. However, compliance does not automatically guarantee readiness during a live cyberattack.
This creates what can be described as a “readiness paradox.” Leaders feel secure because standards are met, but technical teams may lack the hands-on experience required to respond effectively. Several factors contribute to this:
- False Sense of Security: Executives often rely on reports and dashboards that show static metrics. These reports may confirm that controls are in place, but they do not measure how well teams can detect or stop an active attacker. The metrics used for audits are often disconnected from real technical performance.
- The Checklist Trap: Security professionals frequently spend more time documenting policies than practicing response procedures. As a result, they understand what the policy says should be done, but may not feel confident executing those steps under pressure.
- Outdated Skillsets: Cyber threats evolve faster than most training programs. Many professionals are certified in legacy security frameworks or traditional perimeter defenses, yet modern attacks increasingly rely on automation, AI-assisted reconnaissance, and social engineering. When attackers use techniques that weren’t part of earlier training cycles, defenders can feel technically equipped on paper but practically underprepared in reality.
The illusion of compliance-based security persists because certifications are visible and measurable. Operational confidence is harder to quantify. Yet when a real attacker gains access, documentation offers no defense; only practiced capability does.
To strengthen capability, professionals must bridge the gap between theoretical standards and practical defense. The Post Graduate Program in Cybersecurity from The University of Texas at Austin is specifically designed to transform this "checklist" mindset into operational mastery. By moving beyond simple memorization, this 20-week program focuses on the practical application of security controls to build true organizational resilience.
Cyber Security Course by UT Austin for Professionals
Master cybersecurity tools & techniques in UT Austin’s 20-week program. Designed for working pros with hands-on labs, expert guidance & real-world
How This Program Empowers You:
- Master the Frameworks: Deepen your understanding of essential standards like NIST, MITRE ATT&CK, and CIS Benchmarks to ensure your compliance efforts are rooted in defense.
- Build Muscle Memory: Move beyond theory by following Incident Response Playbooks and practicing in hands-on labs that simulate real-world attack scenarios.
- Verify Through Penetration Testing: Learn to view your infrastructure through the eyes of an attacker, scanning for and exploiting vulnerabilities to validate your actual security posture.
The Growing Gap in AI Cyber Readiness
The rapid growth of artificial intelligence has significantly changed the threat environment.
Attackers now use automation and generative AI to create faster and more sophisticated attacks. Security teams that were already under pressure now face threats that move at machine speed.
This shift has increased the feeling of unpreparedness across the industry and has further widened the cybersecurity skills gap.
In fact, according to the World Economic Forum’s Global Cybersecurity Outlook 2026, 94% of leaders identify AI as the most significant driver of change in cybersecurity today. This shift has increased the feeling of unpreparedness across the industry. Key concerns include:
1. AI-Driven Attacks
Organizations are reporting growing anxiety around AI-enabled threats. Automated phishing campaigns can now craft highly personalized messages at scale with other types of cybersecurity attacks. Deepfake audio and synthetic content make impersonation more convincing. Malware can be iterated and modified rapidly to evade detection.
To combat this "AI arms race," the Professional Certificate in Cybersecurity: IT and Data Security in the Age of AI from Johns Hopkins University provides a 14-week specialized framework.
JHU Cybersecurity Certificate Course
Build in-demand cybersecurity skills with JHU experts. Learn AI, cloud, and network security. Hands-on projects. Flexible online format.
This program is specifically designed to equip defenders with AI-powered defense mechanisms and the ability to deploy Generative AI solutions to strengthen enterprise security posture.
How this program prepares you for the age of AI:
- AI-Powered Defense: Learn to leverage agentic AI tools like Darktrace, implement LLM Firewalls, and use AI for advanced incident analysis.
- Counter-AI Tactics: Gain insight into AI-generated malware, AI-powered threats, and the OWASP Top 10 for LLMs to protect your organization from automated adversaries.
- Hands-on Tool Proficiency: Build an e-Portfolio showcasing your mastery of tools like Nessus, Wireshark, AWS Security Hub, and even NotebookLM for security research.
- Cloud & Federal Resilience: Master secure cloud design and understand U.S. federal compliance standards (FedRAMP, CMMC) critical for high-stakes data environments.
2. Speed and Scale
AI allows attackers to test, refine, and deploy attack variations in minutes rather than days. Phishing emails can be generated in thousands of unique versions. Exploit code can be adjusted automatically based on system responses. Many security teams feel their existing tools, processes, and training cycles were not designed for this level of automation and adaptability.
3. Limited Defensive Automation
While attackers rely on automation, defensive responses often remain manual. According to Fortune Business Insights, the market for AI in cybersecurity is projected to reach $44.24 billion in 2026, yet a significant gap remains: roughly one-third of organizations still lack a formal process to validate AI security before deployment. Without AI-powered monitoring and response tools, which are credited with a 74% improvement in detection speed, professionals feel they are at a disadvantage.
The result is a widening imbalance between the speed of attack and the speed of defense. When attackers iterate instantly, and defenders deliberate manually, confidence naturally erodes. The challenge is no longer just about having controls in place; it is about ensuring those controls can operate at the same velocity as the threats they are designed to stop.
The Human Impact: Stress and Burnout
Unlike many other roles, cybersecurity involves defending against intelligent and motivated adversaries who are actively trying to cause harm. This pressure has real consequences, especially when organizations struggle to fill the cybersecurity skills gap through proper hiring and upskilling.
- High Stress Levels: In rapidly growing technology markets, cybersecurity professionals are expected to protect large and complex infrastructures. However, training budgets and structured development programs may not always match these expectations.
- Burnout and Turnover: When professionals feel unprepared, stress increases. Over time, this leads to burnout and higher attrition rates. As experienced employees leave, organizations lose valuable institutional knowledge.
- Lack of Psychological Readiness: Technical knowledge alone is not enough during a crisis. If professionals have never handled a realistic simulation, their first live incident may trigger confusion instead of confident action.
Without proper support, even highly skilled professionals can lose confidence in their ability to manage real incidents.
The Disconnect Between Security Teams And Leadership
Another major challenge is the gap between technical teams and executive leadership. Security professionals often raise concerns about vulnerabilities, outdated tools, or resource shortages. However, these warnings may not always receive immediate attention.
This disconnect appears in several ways:
- Unheard Internal Warnings: Many cybersecurity professionals openly express concerns about their organization’s readiness. They point to outdated strategies and limited resources as ongoing risks.
- Persistent Preparedness Gap: Despite increasing cybersecurity budgets over the years, many organizations still feel unprepared. This indicates that spending alone does not guarantee improvement, especially if investments do not directly address the cybersecurity skills gap.
- Growing Infrastructure Complexity: The adoption of cloud platforms, hybrid work environments, and multiple digital tools has expanded the attack surface. Security teams often struggle to maintain full visibility across these complex systems, leading to blind spots.
When leadership assumes everything is under control, but technical teams feel overwhelmed, readiness suffers.
Moving Toward True Operational Readiness
To close the readiness gap, organizations must shift their focus. Instead of prioritizing compliance alone, they must build real capability and resilience. This transformation requires several practical steps, such as:
1. Continuous Upskilling: Training should not be limited to annual sessions. Teams should be provided with access to various cyber security courses that address modern threats, including AI-driven attacks and advanced social engineering techniques.
2. Competency Over Certification: Certifications have value, but they should not be the only measure of expertise. Practical assessments, such as simulated breach exercises, provide a better understanding of real capability.
3. Empowering Security Operations Centers (SOCs): Security teams need access to automation and advanced detection tools. By reducing the burden of repetitive tasks, analysts can focus on complex investigations and strategic decisions. True readiness is built through practice and skill development, not just documentation.
4. Continuous Red Team Exercises: Regular testing by internal or external red teams helps identify weaknesses before attackers do. Ongoing simulations keep defenders alert and prepared.
5. Industry-Specific Scenarios: Training should reflect the organization’s actual risk profile. For example:
- Financial institutions can simulate payment system breaches.
- Manufacturing companies can test operational technology attacks.
- Healthcare providers can simulate ransomware targeting patient data.
6. Strengthening Executive Involvement: Cybersecurity is not only a technical issue; it is a business risk. Leadership involvement is essential for improving readiness. Important steps include:
- Executive Participation in Simulations:
Leaders should join incident response drills to understand the decisions required during a crisis, such as whether to shut down systems or how to communicate with stakeholders.
- Cross-Department Coordination:
Incident response often involves legal, human resources, public relations, and operations. Without coordination, technical efforts may be delayed by internal confusion. When executives and technical teams work together, organizational confidence improves significantly.
- Investing in the Right Technology:
Technology alone cannot solve every problem, but the right tools can strengthen readiness when combined with skilled professionals. Organizations should prioritize:
- Behavioral Analytics:
Instead of only detecting known threats, modern systems should identify unusual behavior. This helps detect insider threats or compromised accounts early.
- Integrated Platforms:
Using too many disconnected tools increases complexity. Consolidated platforms improve visibility and reduce response time.
- Automation of Routine Tasks:
Automating alert triage and data collection reduces workload and allows analysts to focus on high-value tasks. Smart investments enhance clarity, speed, and decision-making.
Conclusion
The feeling of unpreparedness among cybersecurity professionals is not irrational. It reflects a reality where threats evolve rapidly, while internal processes and training often lag behind.
For too long, organizations have prioritized:
- Tools over talent
- Compliance over capability
- Documentation over practical readiness
True cyber readiness is not achieved by purchasing software or collecting certifications. It is built through continuous training, realistic simulations, strong leadership involvement, and a culture that values practical skill.
The key question organizations must ask is not “Are we compliant?” but “Are we truly ready to respond?”
By investing in people, adopting defensive automation, encouraging cross-functional collaboration, and addressing the cybersecurity skills gap through structured upskilling, organizations can move from paper-based confidence to real operational strength.






