A business analyst is a person who uses data analysis to analyse, understand, and document business processes, goods, services, and software. A business analyst’s job is to assure increased business efficiency through their understanding of both IT and business operations.
Business analysts’ primary responsibilities include analyzing the company’s business requirements, understanding how they integrate with emerging technology, and offering technological solutions to resolve business problems. This list of business analyst interview questions and solutions is intended to get you ready for positions in the real world. You can get ready for some of the most typical questions during business analyst job interviews by reading this. Consequently, continue reading for assistance with the most crucial business analyst interview questions:
Before attending an interview for a business analyst position, one should be thorough about their previous experience in the projects handled and the results achieved. The types of questions asked generally revolve around situational and behavioural acumen. The interviewer would judge both knowledge and listening skills from the answers one presents.
This blog covers the list of frequently asked important business analyst interview questions for freshers as well as experienced candidates that one could face during job interviews.
Basic Business Analyst Interview Questions
What is the role of a business analyst?
Business analysts essentially work as a bridge between different stakeholders in any organization. They clarify and finalize organizational requirements, and assist in project planning, designing, and validating developed components. They possess professional domain knowledge and help sort business needs amongst stakeholders of different domains. Ideally, Business Analysts also engage with business leaders to understand and obtain data-driven solutions to improve efficiency. These changes are applied to processes, products, and services. Altogether, they execute and implement ideas that are both technologically and financially feasible.
What is SRS? What are its key elements?
A System Requirements Specification (SRS) or a Software Requirements Specification can be defined as a document or set of documents that describe the features of a system or software application. SRS aims at providing a high-level idea of the system, its behaviour, business processes, and the performance parameters required for the system.
Some key elements of an SRS are:
- Scope of Work
- Functional Requirements
- Non-Functional Requirements
- Dependency
- Data Models
- Assumptions
- Constraints
- Acceptance Criteria
What is a Requirement?
A Requirement is essentially a targeted solution created to achieve specific business goals and objectives. It acts as an input to various stages of SDLC, which is a project validated by the stakeholders and business users before implementation. It is vital that every requirement is properly documented for future reference purposes.
How do you categorize a requirement to be a good requirement?

A good requirement is the one that clears the SMART criteria, i.e.,
Specific: A perfect description of the requirement, specific enough to be easily understandable
Measurable: The requirement’s success is measurable using a set of parameters
Attainable: Resources are present to achieve requirement success
Relevant: States the results that are realistic and achievable
Timely: The requirement should be revealed in time
What is a Use Case?
A Use Case is a diagrammatic representation of a system describing the process of how a user uses a system to accomplish a set of goals. It is an integral part of software engineering and software modeling techniques, considering it targets the features and the resolution of any possible errors which a user may encounter.
What are the steps required to design a Use Case?
The steps involved in designing a Use Case are:
- Identification of the system users
- Creation of a user profile for each category of users.
- Identification of objectives associated with each user, and their significant roles.
- Creation of use cases for every goal – with a use case template.
- Structuring the use cases
- Review and validation of the users
What are the different types of actors in a use case diagram?
There are two main types of actors that are depicted in a Use case, they are:
- Primary actors, that start the process
- Secondary actors, that assist the primary actor
The actors can also be categorized into four types, they are:
- Human
- System
- Hardware
- Timer
List out the documents used by a Business Analyst in a project.
The various documents used by a Business Analyst are:
a. FSD – Functional Specification Document
b. Technical Specification Document
c. Business Requirement Document
d. Use Case Diagram
e. Requirement Traceability Matrix, etc.
What is Scope creep? What are its causes? How can it be avoided?
Scope creep, also known as requirement creep is a term that is associated with uncontrolled changes or deviations in a project’s scope within the same resource range.
Some possible causes of scope creep include:
- Poor communication
- Improper documentation
Scope creep can be avoided by:
- Proper documentation
- Organized change management
- A prior intimation of changes to the associated parties
- Refrain from Gold Plating, i.e. additions of extra features to existing functionalities
What is the difference between BRD and SRS?

SRS (Software Requirements Specifications) – is an exhaustive description of a system that needs to be developed and describes the software-user interactions. While a BRD (Business Requirements Document) is a formal agreement for a product between the organization and the client.
Name and briefly explain the various diagrams used by a Business Analyst.
- Activity Diagram: It is a flow diagram representing the transition from one activity to another. Here activity is referred to as the specific operation of the system.
- Data Flow Diagram: It is a graphical representation of the data flowing in and out of the system. The diagram depicts how data is shared between organizations.
- Use Case Diagram: Also known as the Behavioural diagram, the use case diagram depicts the set of actions performed by the system with one or more actors (users).
- Class Diagram: This diagram depicts the structure of the system by highlighting classes, objects, methods, operations, attributes, etc. It is the building block for detailed modelling used for programming the software.
- Entity Relationship Diagram: It is a data modelling technique and a graphical representation of the entities and their relationships.
- Sequence Diagram: It describes the interaction between the objects.
- Collaboration Diagram: It represents the communication flow between objects by displaying the message flow among them.
Name different actors in a use case diagram.
Broadly, there are two types of actors in a use case:
a. Primary Actors: Starts the process
b. Secondary Actors: Assists the primary actor
They can further be categorized as:
i. Human
ii. System
iii. Hardware
iv. Timer
Describe ‘INVEST’.
The full form of INVEST is Independent, Negotiable, Valuable, Estimable, Sized Appropriately, and Testable. With this process, the technical teams and project managers deliver quality products or services.
Describe the Gap Analysis.
It is utilized to analyze gaps between the existing system and its functionalities against the targeted system. The gap is inferred to the number of changes and tasks that need to be brought in to attain the targeted system. It compares performance between the present and the targeted functionalities.
What are the various techniques used in requirement prioritization?
Requirement prioritization, as the name suggests, is a process of assigning priorities to the requirements based on business urgency in different schedules, phases, and costs among others.
The techniques for requirement prioritization are:
a. Requirements Ranking Method
b. Kano Analysis
c. 100 Dollar Method
d. MoSCoW Technique
e. Five Whys
What is BPMN? What are its basic elements?
BPMN is the abbreviation for Business Process Model and Notation. It is essentially a graphical representation of business processes. There are five basic elements of BPMN
- Data
- Artifacts
- Flow Objects
- Swimlanes
- Connecting Objects
What is Benchmarking?
Benchmarking is the process of measuring the performance of an organization in order to compete in the industry. This process involves the measure of its policies, performance, rules, and other such parameters.
What are some issues faced by business analysts?
Right from the initiation to post-implementation of a project, a business analyst may face the following problems:
- Employees related problems
- Technology-related problems
- Access related issues
- Business policies-related issues
- Business model errors
Stay tuned to this page for more information on interview questions and career assistance. If you are not confident enough yet and want to prepare more to grab your dream job as a Business Analyst, upskill with Great Learning’s PG program in Business Analytics and Business Intelligence, and learn all about Business Analytics along with great career support.
Differentiate between a Risk and an Issue.
Risk is nothing but a problem or something that can be predicted earlier so that some improvement plans are used to handle them. Whereas, an ‘Issue’ means the risk that had happened or occurred.
Example: On some roads, a few caution boards are stating “Road under repair, take diversion”. This is called Risk.
Define Pareto Analysis?
Also known as the 80/20 rule, Pareto Analysis is an effective decision-making technique for quality control. As per this analysis, it is inferred that 80% of effects in a system are a result of 20% causes, hence the name 80/20 rule. Pareto Analysis is a proper technique used in decision-making for quality control activities and also used in tracing out the resolutions for defects. It is categorized as a decision-making technique based on its statistics that, with a limited number of selected inputs we can have a great impact on the outcome.
Define Kano Analysis.
Kano analysis is a powerful technique used in classifying the various types of customer requirements for new products. This Kano Analysis deals with the needs of the end-users of the product.
The main attributes of this Kano Analysis are
- Threshold Attributes: These are the properties that a customer wants to be available in the product.
- Performance Attributes: These represent some extra properties that are not necessary for a product but can be added for customers’ enjoyment.
- Excitement Attributes: These are the properties that the customers are not aware of but are excited about when they found such properties in their product.
Differentiate between Fish Model and V Model?
| Fish Model | V model |
| The fish model is comparatively very costly and time-consuming | V model requires less time and cost |
| The fish model is used when there were no ambiguities in the customer’s requirements | Otherwise, the V model is preferred. |
Explain Black Box Testing
Black box testing is a kind of testing where the entire unit is tested as a whole without considering the contents or how the inner components and units are tested. This testing method only focuses on the known input signal and checks whether the output behavior is according to expectation or not.
Which model is better Waterfall model or Spiral Model?
It is selecting the life cycle model for any project which should be based on its scope, type, and limitations. It is dependent on the culture of the organization, its policies and terms, and conditions, and the process of developing the system.
Which method is mostly used for the assessment or evaluation of a prospective vendor?
In the business analysis process Vendor, the Assessment technique is a more fruitful method.
Explain critical path analysis.
A project that involved a set of activities from Start to Finish. A critical path is a set of activities that includes the longest path in the entire project.
Difference between Software Development Lifecycle and Project Lifecycle
| Software Development Lifecycle | Project Lifecycle |
| Helps you to develop particular software products. | Allows you to develop a new product in the business. |
| It involves single software across different phases. | It Involves multiple software in a single customer scenario. |
| SDLC phases are requirement gathering, coding, documentation, operations, and maintenance. | Project lifecycle phases are Idea generation, screening, development, testing, and analysis. |
What is the best way of using an Activity Diagram?
It successfully captures and represents visually the flow of users in a system. The best way of using it is at the conceptualization stages.
When would you use Pugh Matrix?
It is a decision-making method that helps in the evaluation of advantages and disadvantages against a reference system.
Why is benchmarking required?
It is required to set standards for a company. It helps match policies with performance. It is required to set standards for a company. It helps match policies with performance. Benchmarking is considered as important as it showcases the performance of an organization when juxtaposed against its competitors. Various governing metrics such as performance, goals, and other measures can be used as a guide.
Explain the steps that turn an idea into a product?
The steps include Market Analysis, Competitor Analysis, SWOT Analysis, Personas, Strategic Vision and Feature Set, Prioritize Features, Use Cases, SDLC, Storyboards, Test Cases, Monitoring, and Scalability. The role of personas and feature prioritization is extremely crucial.
When do you use the Pair-choice technique?
This is a prioritization technique. Its main aim is to identify the most important items in a process. It is usually determined by the key stakeholders. A comparative analysis helps to analyze different metrics to assign significance.
Are you familiar with the difference between pool and swimlane?
In an activity diagram, pool denotes a single person engrossed in one activity, however, swimlane means activities among groups
How do you manage scope creep?
It is best to avoid scope creep through constant and vigilant project management. In case of scope creep or deviation, steps should be taken to arrest the development of scope creeps to cut down on further damages. It can be done by following proper protocol and documentation.
What are the skills that a business analyst must possess?
We can broadly categorize the skills of a business analyst in three types:
- Fundamental skills
- Technical skills
- Business Analysis skills
| Skill category | Skills |
| Fundamental Skills | Problem Solving Communication Management skills Research |
| Technical skills | IT skills like MS Office, Operating systems, Programming languages, Knowledge of databases, SDLC knowledge, Domain knowledge |
| Business Analysis skills | Requirement Elicitation Documentation Decision making Creativity Analytical skills |
Which documents are used to capture non-functional requirements?
There are two documents that are used to capture non-functional requirements, and they are:
- SDD (System Design Document)
- FRD (Functional Requirement Document)
What is UML modeling?
UML stands for Unified Modelling Language. It is a standard that the industry uses for documenting, constructing and visualizing various components of a system. This modeling standard is primarily used for software development. However, it is also used for describing job roles, organizational functions, and business processes. Some of the important diagrams that BAs use as part of UML are the class diagram, state diagrams, and use cases.
What are the best practices to follow while writing a use case?
- To become a valid use case, the use case must provide some value back to the actor or stakeholder.
- The functional and non-functional requirements must be captured appropriately in the use case.
- The use case must have one or more alternate flows along with the main flow.
- The use case should only describe what the system does and not how it is done which means it will not describe the design. It will act as a black box from the viewpoint of an actor.
- The use case should not have any, i.e. it should be stand-alone.
What is the difference between exception flow and alternate flow?
Alternate flows are the alternative actions that can be performed apart from the main flow and can be considered an optional flow.
Exception flow is the path traversed in case of any exception or error.
What are the different types of gaps that a business analyst can encounter during gap analysis?
There are mainly four types of the gap–
- Performance Gap – The difference between expected performance and the actual performance
- Product/Market Gap – The gap between budgeted sales and actual sales is termed a product/market gap
- Profit Gap – The variance between the targeted and actual profit of the company.
- Manpower Gap – The gap between the required number and quality of workforce and actual strength in the organization
How do you decide that as a business analyst you have gathered all the requirements?
We can conclude that all the requirements are gathered only when –
- It is validated and approved by the business users.
- The requirements are appropriately aligned with the project’s business requirements.
- The requirements can be implemented with the available resources.
- All the key business stakeholders are aligned with the elicited requirements.
How do you perform requirement gathering?
The requirement gathering process is generally divided into multiple steps which are agnostic to the SDLC cycle. Each step involves:
- specific tasks to perform
- principles to follow
- documents to produce
Explain each step involved in requirement gathering?
Step 1: Gather Background Information – This may include collecting background information about the project, and analyzing any potential risk associated with the project. Techniques like PESTLE analysis and Porter’s Five forces framework could be used for this purpose.
Step 2: Identify Stakeholders – They are the decision-makers of a project and approvers for requirements and priorities. Stakeholders may range from project owners to senior managers, end-users, and even competitors.
Step 3: Discover Business Objectives – This is to understand the business needs of the project before going deep into the project. SWOT analysis, Benchmarking, analyzing business objectives SMART, and listing business objectives are some of the techniques used for this purpose.
Step 4: Evaluate Options – This is to identify the options to achieve business objectives. Impact analysis, Risk analysis, and Cost-benefit analysis are some of the methods which are used for this purpose.
Step 5: Scope Definition – A scope is a project development goal which is set based on the business objectives. A scope definition document is used to detail the goals for each phase of a project.
Step 6: Business Analyst Delivery Plan – Based on the project scope, stakeholders’ availability, and project methodology a document called business analyst is created at this step. The document provides information on deliverables with their timeline.
Step 7: Define Project Requirements – In this step, two types of documents are used – A functional requirement document and a Non-functional requirement document. Based on the development methodology to be used in the project the business analyst needs to clarify the requirements with the stakeholders by interviewing them on the requirements and getting the sign-off on the same.
Step 8: Support Implementation through SDLC – This is the technical implementation step of the requirements where a business analyst gets involved with different teams. This includes coordinating with the development team and testing team to ensure requirements are implemented as expected and appropriately tested against all the possible business scenarios. They also need to handle the change request which may arise from the stakeholders at a later point in time.
Step 9: Evaluate Value Added By Project – This is the continuous evaluation of the project to evaluate whether the business objectives implementation correctly meets the business needs outcome and timeline.
Why it is necessary for a business analyst to get involved during the implementation of requirements?
Gaining domain knowledge and providing an analytical solution are the two major criteria of a business analyst. Hence, during the actual implementation of a requirement or use case a business analyst can help to resolve many business strategies-related problems that may arise during the implementation stage. On the contrary, they can learn from the problems which may help them to provide the solution in similar scenarios and also help to gain their domain knowledge.
What are the problems that a business analyst may face?
From the initiation to post-implementation of a project, a business analyst may face the following problems –
- Employees related issues
- Technology-related problems
- Access related
- Business policies-related issues
- Business model errors
Explain the requirement elicitation strategy?
Requirement elicitation is the process to collect all the requirements related to a system from the end-users, customers, and stakeholders. As per the BABOK guide, there are nine methods that can be used as part of the requirement elicitation process, and these are:
- Brainstorming
- Interviews
- Observation
- Document Analysis
- Focus Groups
- Requirements Workshops
- Interface Analysis
- Survey or Questionnaire
- Prototyping
What is the difference between Business analysis and Business Analytics?
The key difference between Business analysis and Business analytics is the first one is more functions and process-related whereas the second one is data related.
Business analysis – recognizes business needs and determines the solutions to that problems. Tools and techniques like SWOT, PESTEL, CATWOE, MOST, FIVE WHY, etc. are used for business analysis.
Business analytics – handles data and analyzes data to get insights into a business. Finally, it generates reports. Mainly four types of business analytics are used, and they are – descriptive analytics, decisive analytics, prescriptive analytics, and predictive analytics tools and technologies like Big data, and BI is used for this purpose.
Also, check out the difference between business analysts and data scientist
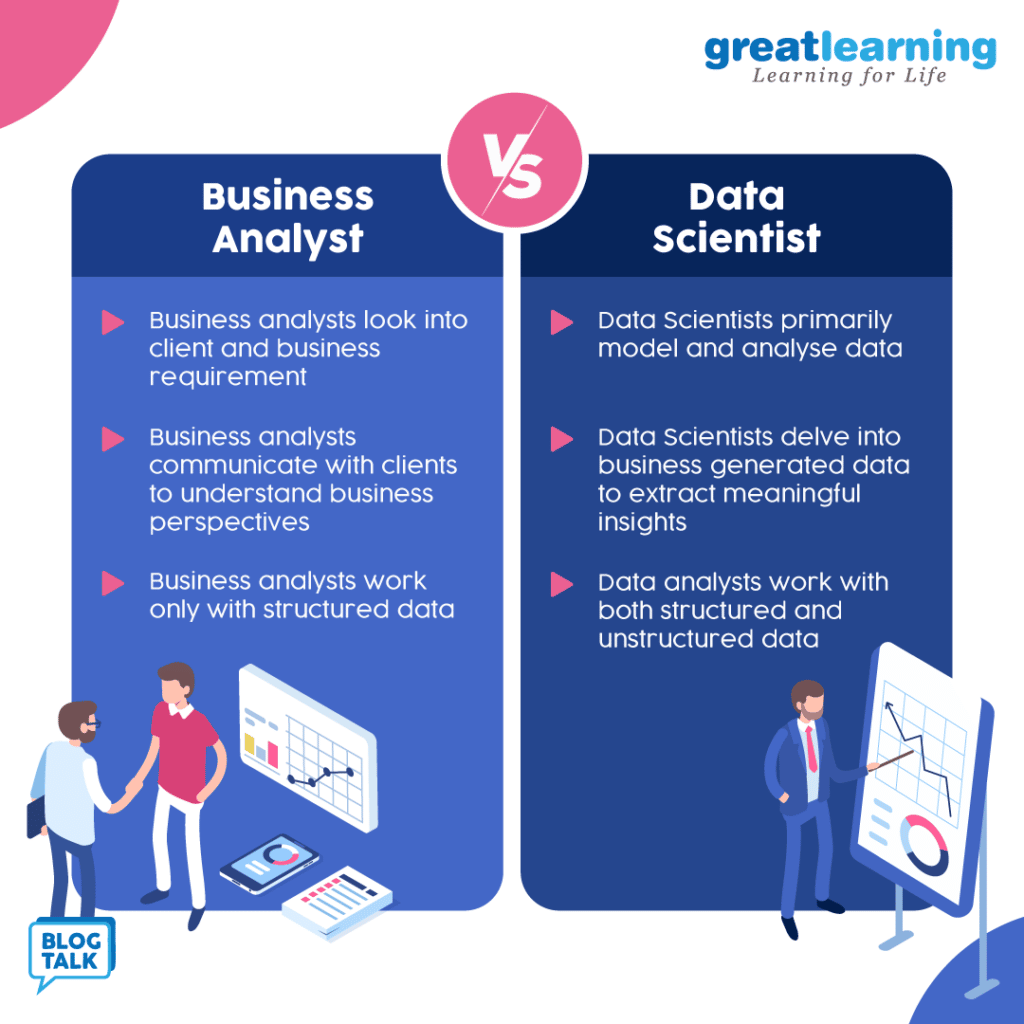
What are the effective skills to solve any problem as a business analyst?
- Leadership skill
- Excellent communication skill
- Problem analysis skill
- Technical knowledge
- Domain knowledge
Business Analyst Interview Questions For Experienced
What is the Agile Manifesto?
Agile Manifesto is a software guide about the Agile development principles which ensure iterative solutions.
What are the essential qualities of an Agile BA?
An Agile BA must be able to:
- The BA is expected to collaborate with product owners and developers to elicit requirements. The BA also must work to develop real functional requirements.
- The BA must do requirement elicitation in an iterative way
- The BA must make requirement specifications, data models, and business rules as much lightweight as possible.
- The BA must be technically sound so that he can understand how the components of the system interact with each other. Besides that, he must understand the agile terminologies as he acts as the middleman between the customer and the project team.
- The BA must concentrate on the just-enough requirement and test criteria to meet the just-in-time delivery goal of an agile project.
When should you use the Waterfall model instead of Scrum?
If the requirement is simple and specific, we should go for the Waterfall model instead of Scrum.
What are the four key phases of business development?
The four key phases of business development:
- Forming
- Storming
- Norming
- Performing
What do you know about Kanban?
Kanban is a tool that helps the agile team visually guide and manage the work as it progresses through the process. Besides, it works as a scheduling system in Agile just-in-time production. The Kanban board is used to describe the current development status.
Mention some of the most important agile metrics?
The following are some important agile Matrices
- Velocity – This is used to track the progress of a project
- The sprint burndown matric – This helps to track the work done with the sprint.
- The priority of the work
- Work category allocation – This metric helps to get an idea about the priority of the work and work category allocation.
- The cumulative flow diagram – the uniform flow of work can be checked through this diagram of cumulative flow. Here the x-axis represents time and the y-axis stands for the number of efforts.
- Defect removal awareness – This helps to produce quality products.
- Business value delivered – This is used to estimate the work efficiency of the team. It associates 100 points for measurement.
- Time coverage – It estimates the amount of time invested in coding during testing. It is the ratio of the number of lines of code called by the test suite to the number of relative lines of codes.
- Defect resolution time – This is the turnaround time for detecting and fixing bugs. There processes involved in for this purpose are:
- bug fixing
- eliminating the bug
- Scheduling a fix
- Defect fixation
- Handover of the resolution report
Is there any difference between incremental and iterative development?
In an iterative development software development happens without any interruption. Here the software development cycles which typically consist of sprint and release are repeated until the final product is obtained. Whereas, in an incremental model, software development follows the product design, implementation, and testing incrementally until the product is finished. Hence, it involves development and maintenance.
Difference between extreme programming and scrum?
Scrum and extreme programming both follow iterations which are known as sprints. However, the sprints in a Scrum process last up to two weeks to one month long whereas in extreme programming (XP) teams the iteration lasts for one or two weeks. Extreme programming is more flexible than Scrum as Scrum does not allow any change in during iterations.
Though we have categorized the above business analyst interview questions based on the experience levels, however, it could be mixed and matched for any career level depending on the organization and their requirement.
Differentiate between risk mitigation and risk avoidance.
| Risk Mitigation | Risk Avoidance |
| Risk mitigation is what to do when a risk occurs. | Risk avoidance is what to do to avoid the risk. |
| It reduces the probability of risk occurrence. | It avoids the risk by eliminating the cause. |
| It checks whether any impact occurs on the project/business. | The impact of the threat occurrence is reduced to 0%. |
| Cost is high in case any risk occurs. | Cost is eliminated in risk avoidance. |
How does CATWOE help in business analysis and decision-making?
Customers, Actors, Transformation process, Worldview, Owners, and Environmental constraints (CATWOE) helps in making decisions ahead of time. It includes analyzing how those decisions will affect customers (C); who are involved as actors (A); what different transformation (T) processes are which might affect the system, global picture, and worldwide (W) issues; who is responsible/has ownership (O) for the business; and what the environmental (E) impacts will be of the project/business.
What is the RUP methodology?
Rational Unified Process (RUP) is a product application improvement method with numerous devices to help with coding the last product and assignments identified with this objective. RUP is an object-oriented approach that guarantees successful project management and top-notch software production.
What is RAD methodology?
The rapid Application Development (RAD) model is a kind of incremental model. The phases of a project are produced in parallel as individual projects. The developments in the project are timeboxed, delivered, and afterward assembled into a working model.
List the components of the Requirements Work Plan.
- Project description
- Key issues
- Deliverables
- Goals and objectives
- Strategy
- Resources
- Budget and time
List the elicitation techniques in Business Analytics
Elicitation is a practice of collecting requirements from end customers and stakeholders; it is a requirement-gathering process. Various techniques involved in this are:
- Brainstorming
- Document analysis
- Focus group
- Interface analysis
- Interview
- Observation
- Prototyping
- Requirements workshop
- Reverse engineering
- Survey
How well can you explain System Analysis in a business?
It is nothing but a simple process of interpretation of the business needs and all the rules imposed by the management for the use of technical systems. The restrictions largely matter and businesses should pay very close attention to the same.
As a Business Analyst, what are your views on the inter-organization migration of employees?
Well, sometimes the problems declare their presence because of no other reason than no proper resources. In the current time, most of the members of a business workforce have good technical knowledge. Even employees have the interest to work with other departments in some cases. Migrating the employees from one department to another is generally not common but it can solve a very large number of business problems if this is managed by a team of experts. Business Analysts often perform this task to get the best possible outcome.
Do you think a Business analyst should be engaged in testing and integrating new solutions?
Of course, this is because a business analyst has the right knowledge about the challenges associated with most of the tasks. Very useful information can be driven and the testing procedures can be made more useful. In addition to this, a business analyst can simply guide an organization on what better can be done in a solution while it is under a test.
What according to you are the basic needs of a Business Analyst to accomplish his/her task?
A Business Analyst can have some basic requirements and they can be
1. Availability of the case scenarios
2. Access to logical data models
3. Data flow diagrams of the problems
4. Reports
5. Work Instructions
What is the difference between post-implementation and pre-implementation problems of a project? What is the role of a BA in managing them both?
The problems that declare their presence before a project is actually executed or implemented are known as pre-implementation problems while the ones that come after the implementation of the same are post-implementation problems. Well, most of the problems come after the implementation of a project. A good Business Analyst cannot overcome them all but can impose a limit on the same. In fact, a BA always works to make sure that both the pre and post-implementation problems can be avoided up to a great extent within the minimum possible time.
What is Pugh Matrix?
Pugh Matrix – Helps to decide the most optimal & alternate product solutions. As this technique is a standard line of the Six Sigma technique, it is known as the design matrix/problem.
What are the advantages of using R for business analytics?
R provides a wide variety of statistical (linear and nonlinear modelling, classical statistical tests, time-series analysis, classification, clustering, …) and graphical techniques, and is highly extensible. The S language is often the vehicle of choice for research in statistical methodology, and R provides an Open Source route to participation in that activity.
One of R’s strengths is the ease with which well-designed publication-quality plots can be produced, including mathematical symbols and formulae where needed. Great care has been taken over the defaults for the minor design choices in graphics, but the user retains full control.
Explain the R environment.
R is an integrated suite of software facilities for data manipulation, calculation, and graphical display. It includes
- an effective data handling and storage facility,
- a suite of operators for calculations on arrays, in particular, matrices,
- a large, coherent, integrated collection of intermediate tools for data analysis,
- graphical facilities for data analysis and display either on-screen or on hardcopy, and
- a well-developed, simple, and effective programming language that includes conditionals, loops, user-defined recursive functions, and input, and output facilities.
What does “Data Cleansing” mean? What are the best ways to practice this?
The best ways to clean data are:
- Segregating data, according to their respective attributes.
- Breaking large chunks of data into small datasets and then cleaning them.
- Analyzing the statistics of each data column.
- Creating a set of utility functions or scripts for dealing with common cleaning tasks.
- Keeping track of all the data cleansing operations to facilitate easy addition or removal from the datasets, if required.
What is the difference between data profiling and data mining?
Data Profiling focuses on analyzing individual attributes of data, thereby providing valuable information on data attributes such as data type, frequency, and length, along with their discrete values and value ranges. On the contrary, data mining aims to identify unusual records, analyze data clusters, and sequence discovery, to name a few.
What is the KNN imputation method?
KNN imputation method seeks to impute the values of the missing attributes using those attribute values that are nearest to the missing attribute values. The similarity between two attribute values is determined using the distance function.
What should a data analyst do with missing or suspected data?
In such a case, a data analyst needs to:
- Use data analysis strategies like the deletion method, single imputation methods, and model-based methods to detect missing data.
- Prepare a validation report containing all information about the suspected or missing data.
- Scrutinize the suspicious data to assess their validity.
- Replace all the invalid data (if any) with a proper validation code.
Define Outlier
A data analyst interview question and answers guide will not be complete without this question. An outlier is a term commonly used by data analysts when referring to a value that appears to be far removed and divergent from a set pattern in a sample. There are two kinds of outliers – Univariate and Multivariate.
The two methods used for detecting outliers are:
- Box plot method – According to this method, if the value is higher or lesser than 1.5*IQR (interquartile range), such that it lies above the upper quartile (Q3) or below the lower quartile (Q1), the value is an outlier.
- Standard deviation method – This method states that if a value is higher or lower than mean ± (3*standard deviation), it is an outlier.
What is “Clustering?” Name the properties of clustering algorithms.
Clustering is a method in which data is classified into clusters and groups. A clustering algorithm has the following properties:
- Hierarchical Clustering
- Hard and soft
- Iterative
- Disjunctive
Define “Collaborative Filtering”.
Collaborative filtering is an algorithm that creates a recommendation system based on the behavioural data of a user. For instance, online shopping sites usually compile a list of items under “recommended for you” based on your browsing history and previous purchases. The crucial components of this algorithm include users, objects, and their interests.
Check out why recommendation system is used in the companies
Name the statistical methods that are highly beneficial for data analysts?
The statistical methods that are mostly used by data analysts are:
- Bayesian method
- Markov process
- Simplex algorithm
- Imputation
- Spatial and cluster processes
- Rank statistics, percentile, outliers detection
- Mathematical optimization
What is a hash table collision? How can it be prevented?
This is one of the important data analyst interview questions. When two separate keys hash to a common value, a hash table collision occurs. This means that two different data cannot be stored in the same slot.
Hash collisions can be avoided by:
- Separate chaining – In this method, a data structure is used to store multiple items hashing to a common slot.
- Open addressing – This method seeks out empty slots and stores the item in the first empty slot available.
How should you tackle multi-source problems?
To tackle multi-source problems, you need to:
- Identify similar data records and combine them into one record that will contain all the useful attributes, minus the redundancy.
- Facilitate schema integration through schema restructuring.
Mention the steps of a Data Analysis project.
The core steps of a Data Analysis project include:
- The foremost requirement of a Data Analysis project is an in-depth understanding of the business requirements.
- The second step is to identify the most relevant data sources that best fit the business requirements and obtain the data from reliable and verified sources.
- The third step involves exploring the datasets, cleaning the data, and organizing the same to gain a better understanding of the data at hand.
- In the fourth step, Data Analysts must validate the data.
- The fifth step involves implementing and tracking the datasets.
- The final step is to create a list of the most probable outcomes and iterate until the desired results are accomplished.
What are the characteristics of a good data model?
For a data model to be considered as good and developed, it must depict the following characteristics:
- It should have predictable performance so that the outcomes can be estimated accurately, or at least, with near accuracy.
- It should be adaptive and responsive to changes so that it can accommodate the growing business needs from time to time.
- It should be capable of scaling in proportion to the changes in data.
- It should be consumable to allow clients/customers to reap tangible and profitable results.
Explain “Normal Distribution.”
One of the popular data analyst interview questions. Normal distribution, better known as the Bell Curve or Gaussian curve, refers to a probability function that describes and measures how the values of a variable are distributed, that is, how they differ in their means and their standard deviations. In the curve, the distribution is symmetric. While most of the observations cluster around the central peak, probabilities for the values steer further away from the mean, tapering off equally in both directions.
What are the advantages of version control?
The main advantages of version control are –
- It allows you to compare files, identify differences, and consolidate the changes seamlessly.
- It helps to keep track of application builds by identifying which version is under which category – development, testing, QA, and production.
- It maintains a complete history of project files that comes in handy if ever there’s a central server breakdown.
- It is excellent for storing and maintaining multiple versions and variants of code files securely.
- It allows you to see the changes made in the content of different files.
How can a Data Analyst highlight cells containing negative values in an Excel sheet?
The final question in our data analyst interview questions and answers guide. A Data Analyst can use conditional formatting to highlight the cells having negative values in an Excel sheet. Here are the steps for conditional formatting:
- First, select the cells that have negative values.
- Now, go to the Home tab and choose the Conditional Formatting option.
- Then, go to the Highlight Cell Rules and select the Less Than option.
- In the final step, you must go to the dialogue box of the Less Than option and enter “0” as the value.
Differentiate between variance and covariance.
Variance and covariance are both statistical terms. Variance depicts how distant two numbers (quantities) are in relation to the mean value. So, you will only know the magnitude of the relationship between the two quantities (how much the data is spread around the mean). On the contrary, covariance depicts how two random variables will change together. Thus, covariance gives both the direction and magnitude of how two quantities vary with respect to each other. Check out the difference between covariance and correlation.
Explain univariate, bivariate, and multivariate analysis.
Univariate analysis refers to a descriptive statistical technique that is applied to datasets containing a single variable. The univariate analysis considers the range of values and also the central tendency of the values.
Bivariate analysis simultaneously analyzes two variables to explore the possibilities of an empirical relationship between them. It tries to determine if there is an association between the two variables and the strength of the association, or if there are any differences between the variables and what is the importance of these differences.
Multivariate analysis is an extension of bivariate analysis. Based on the principles of multivariate statistics, the multivariate analysis observes and analyzes multiple variables (two or more independent variables) simultaneously to predict the value of a dependent variable for the individual subjects.
How can a Data Analyst highlight cells containing negative values in an Excel sheet?
A Data Analyst can use conditional formatting to highlight the cells having negative values in an Excel sheet. Here are the steps for conditional formatting:
- First, select the cells that have negative values.
- Now, go to the Home tab and choose the Conditional Formatting option.
- Then, go to the Highlight Cell Rules and select the Less Than option.
- In the final step, you must go to the dialog box of the Less Than option and enter “0” as the value.
How would you plan to work with a difficult stakeholder?
There is a good chance that you will have to work with many people with different personalities. It becomes essential that you address your answer in a structured way:
- Talk positively about the situation at hand and how you aim to deal with it.
- Adds value to explain the situation in detail if required.
- Talk about a plan of action that you think best fits the situation.
- Talk about how your actions can lead to an excellent solution to the problem at hand.
Why is analytical reporting critical?
Since business analysis is a domain that aims to solve problems by using data, reporting is used to add value by providing concrete information, results of analytics, and recommendations in a structured manner. These reports can later serve as a foundation for stakeholders to decide upon a course of action.
Have you previously worked with SQL?
SQL is an essential part of working with database management systems. It allows for an easy working pipeline when it comes to structured data.
SQL is vital for a business analyst as it helps showcase your proficiency when handling a large amount of data. You must state examples of your previous usage of SQL to add value to your answer.
According to you, which are the essential business analysis tools out there today?
This question is aimed toward understanding your foundational knowledge and familiarity with the latest standards out there. There are many tools that you can choose from to answer this question:
- MS Excel
- MS Visio
- SQL Server
A vital thing to note here that you should always incorporate your own skills and experiences with the tools that you mention.
What is the use of activity diagrams and use case diagrams in business analysis?
Activity diagrams are used to showcase the various activities that go on with respect to multiple departments in the organization. While use case diagrams are used as an assessment tool to visualize the requirements of a system and to help in making decisions based upon the priorities and tasks at hand.
What is the most important thing to note when approaching a new project?
To begin with, it adds an immense amount of value to understanding the requirement at hand. The planning stages of the project require a good amount of breakdown to keep it simple across the board.
An important thing to think about is how you would have to take certain specific steps to meet the needs of the project at hand.
Vital to talk about contingency planning and to make sure that you aim the answer to helping the client out by fulfilling their requirements and also help meet the employer’s goals at the same time.
What is the use of the BCG matrix?
BCG is an abbreviation for Boston Consulting Group. This is a matrix structure that helps in performing an in-depth analysis of products and business processes.
They are very much popular for their usage in:
- Brand marketing
- Portfolio analysis
- Strategic analysis
What is the meaning of OLTP?
OLTP is an abbreviation for Online Transaction Processing. It is a system that is widely used to perform transactions on a database. They are very important systems that help in the rapid addition and removal of data from the database.
Which of the following is better for a project – The spiral model or the Waterfall model?
The question at hand and the answer to the same is completely dependent on the project at hand. There can be many cases where the waterfall model outshines the spiral model or even vice versa.
Depending on the requirements at hand, it becomes an obligation to check which model best fits the project and then to work on a plan to implement that.
Are flowcharts important in the field of business analysis?
Yes, flowcharts are very important in this domain. It is used to express complex relationships in a linear fashion allowing for greater understanding by both technical and non-technical parties involved in the projects.
Are there any shortcomings of using analytical reporting?
Analytical reporting is used to provide a good amount of insight into a process. However, it becomes difficult to assure the occurrence of the outcome indicated by the reports. Also, the reports are directly dependent on the data at hand. If the data is inaccurate, then the results can seem skewed.
What is the meaning of FMEA and how is it used?
FMEA is an abbreviation for Failure Mode and Effects Analysis. It is an important part of business analysis that is used to showcase the contingency plans in terms of failure occurrence and its impact on the system.
What is the abbreviation of SQUARE in business analysis?
SQUARE is an abbreviation for Security Quality Requirements Engineering. It is an important step in this domain that helps to document the requirements in terms of security for the system.
In terms of efficiency with respect to time, is it the V model that is efficient of the Fish model?
In the majority of the cases, the V Model is considered to be efficient in terms of time consumption when directly juxtaposed with the Fish model.
What is a bigger threat – issue or risk?
The answer to this question has a direct dependency on the project at hand. Issue talks about the outcome of the events that have already occurred while a risk projection talks about a future event that is yet to occur.
The SRS document is derived from BRD – True or False?
True. The Software Requirements Specification (SRS) document is derived from the BRD after the business analysts interact with the client regarding the requirements of the project at hand.
What is the meaning of a market gap when performing gap analysis?
Market gap is the difference that exists between actual sales numbers and values and the estimated sales numbers and values. It is vital to bridge this gap and can be done so by analysing the various metrics.
What are the varieties of techniques that are used for requirement prioritization?
There are many documents used for requirement prioritization:
- Five Whys
- Kano Analysis
- MoSCoW Technique
- Requirements Ranking Method
Is it important to spend time on designing a good alternate flow in the use case diagrams?
Yes, it is very important to have a good alternate flow. It consists of the use cases that have to be followed in the situation where the primary requirement of the system fails.
Can exception flow be considered the same as alternate flow?
No. Even though the concepts sound similar, they cannot be considered the same. Alternate flow talks about situations where system failure occurs while exception flow talks about correction if there is an occurrence of an error or an exception.
What are some of the important metrics in agile that add value to the process?
There are many important agile metrics:
- Priority of work
- Defect resolution time
- Spring burndown matrix
- Business value delivery
To Conclude
With this, we have to come to the end of the Business Analyst Interview Questions blog. We hope that this helps you in preparing for your interview and that you pass it with flying colours. All the best and keep learning with Great Learning Academy.





